
A SECURED PAYMENT GATEWAY TO AVOID FRAUDULENT TRANSACTIONS
This article can be divided mainly into 2 sections.
- One, Project Synopsis, you are here 😊
- Two, Project demonstration
PART 1: Project Synopsis
Payment Gateways/Payment Portals have become essential to the security of businesses that accept online payments. But online fraud has risen drastically and is wrongful and even it is a criminal deception that is intended for personal or financial gain. These payments are performed online over the Internet.

Debit/Credit card fraud is the most common type of fraud nowadays. It is basically when a fraudster steals card details and buys goods online or even transfers money 💳. However many companies offer only basic security measures to reduce such debit/credit card frauds.
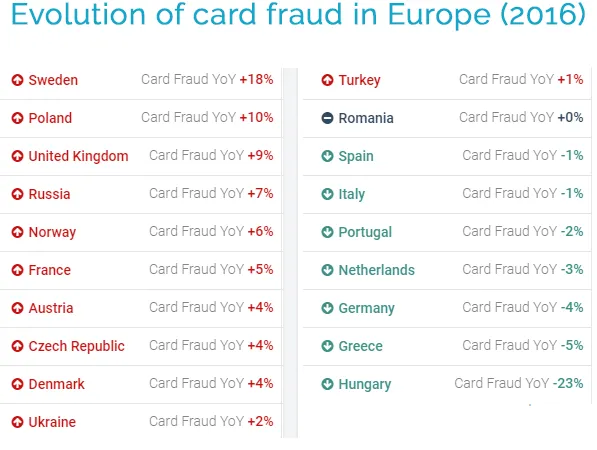
Credit card fraud continues to be one of the most common types of online scams that plague businesses all over the world. It is even a form of Identity Theft. Online credit card fraud happens when a criminal steals someone’s physical card and Personal Identification Number (PIN) to make an unauthorized transaction or even withdraw funds from the victim’s account without his/her consent.
Hence it is essential to develop a payment gateway or modify an existing one and incorporate more features that offer better security and quality fraud protection 🔐.
In the current payment gateways, Card Not Present payment (CNP) is used in which the below fields are prompted.
- Name on the Card
- Credit Card Number
- Expiry Date
- CVV
On providing these details, it directs to a One-Time Password (OTP) authentication process. Once the OTP received is provided, the transaction is executed and made successful.
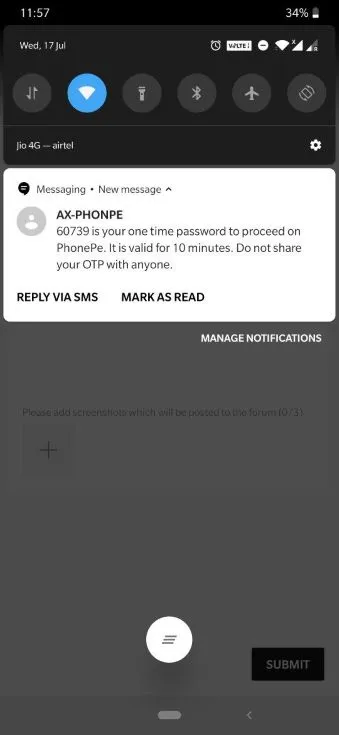
A criminal who stole the credit card can easily input these fields and a person who has access to the mobile phone can also provide the OTP too.
This is possible because an OTP is sent as a push message to the mobile phone and without unlocking it, the message can be viewed from the screen itself.
Therefore, it is essential to develop a secured payment gateway to avoid online fraud and it should have the capability to restrict and block the transaction performed by the attacker using genuine user’s credit card details i.e., the gateway should try to detect fraudulent transactions before the transaction succeeds 🚫. However, it is hard to detect credit card fraud beforehand. Some clues can help in recognizing fraudulent credit card transactions and if a customer exhibits many of these suspicious behaviors, the transaction might potentially be considered fraudulent 💡.
With E-Commerce, all transactions are considered Card-Not-Present because the physical card or the cardholder is not present. And therefore, you have to trust that the true cardholder is the one authorizing each transaction. Because of this, CNP transactions pose a greater risk for such online fraud!
How does it work?

Concept of Behavior and Location Analysis (BLA) is used in this application. The previous individual transaction details are not known to any Fraud Detection System (FDS) running at the payment portals. Hence, BLA is used for addressing this weak point.
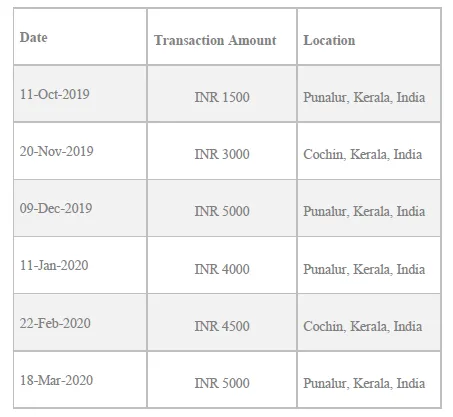
User spending patterns and Geographical location are used to verify the user’s identity. If any unusual pattern is detected, the system requires re-verification by providing certain details for security purposes. And, if re-verification fails, the system will block the user after 3 invalid attempts.
Apart from BLA, the below concepts also aid in reducing online fraud-related losses:
- Address Verification Service (AVS) 📍
AVS is one of the effective measures to detect online fraud and ensure security. When customers purchase items, they need to provide their billing address and postcode. An AVS will check if this address matches the card-linked address. In short, it is used to verify the address and postcode, as entered by the user, with the proof of the address to which card statements are usually sent. If there is no match or only a partial match in some cases, it may denote that the user is not the actual cardholder.
- Device Identification
Device identification analyzes the computer rather than the person who is visiting the website. It profiles the operating system to gauge if the online transaction has to be approved or declined. All devices such as phones, computers, tablets, etc., have a unique device fingerprint, that helps to identify fraudulent patterns and assess risks if any. It is also possible to check whether people have flagged the device for suspicious or fraudulent activity before. Also, fraudsters cannot impersonate a machine’s unique identity, thus making it a pivotal point for protecting one’s business against online fraud.
- Negative Database Security
Negative database security allows you to match each transaction against a list of high-risk IPs, card numbers, and contact information i.e., any card numbers or other details, such as cardholder’s name/address, which have been flagged in the past and put on the ‘blacklist’, will be blocked from the transaction🤚.
This application does not require fraud signatures and is able to detect frauds by considering a cardholder’s spending habit. Another important advantage of BLA based approach is that there is a drastic reduction in the number of false positive transactions identified as malicious by an FDS.
Project Category
Information Security — Strategies for reducing online fraud-related loss.
Research Methodology
The project will focus on developing a web application that acts as a mock secured payment gateway for online transactions to avoid debit/credit card fraud. In this proposed system, I will be using the following concepts to check for unusual patterns during an online transaction:
- Behavior and Location Analysis (BLA)
- Address Verification Service
- Device Identification
- Negative Database Security
Research Environment Details
Technologies/Tools:
- Eclipse IDE — Oxygen (Release 4.15)
- MySQL Server — Version 8.0.20
- MySQL Workbench 8.0.20 for GUI
- Spring MVC framework 5.1
- Hibernate framework 5.4
- Java 8 (jdk-13 and jre1.8.0_231)
- Apache Tomcat 9
- Spring Data JPA 2.1.5 (Java Persistence API)
- Java Servlet 3.1 and Java Servlet JSP 2.3.1
- Maxmind GeoIP 2.12.0
Operating System:
- Windows version 7 and above
First, a web application is developed which will have two modules — Admin and User. All the data stored in the database are encrypted using Advanced Encryption Standard (AES).
The admin,
- can view/add/edit/delete the blacklisted data (IP, Card Number, Card Holder Name, and Card Holder Address) and can even generate a report from it for the cybersecurity team – (Negative Database Security)
- can block/unblock accounts
- can view/add/edit/delete login details, view/edit/delete customer card details, and view/delete user transaction history details
Various e-commerce websites or any other websites that require a payment gateway can integrate with this application which will be our revenue model💲. If a user has logged in to the e-commerce, once they are ready to checkout, the website redirects to our web application and automatically logs in to the user module. The page then prompts the user to input card details:
- Card Holder’s Name
- Card Number
- Card Expiry Date
- CVV
- Transaction Amount
- Billing Address
The following operations are then performed:
1. Analyzing credit card owner’s previous transaction rates
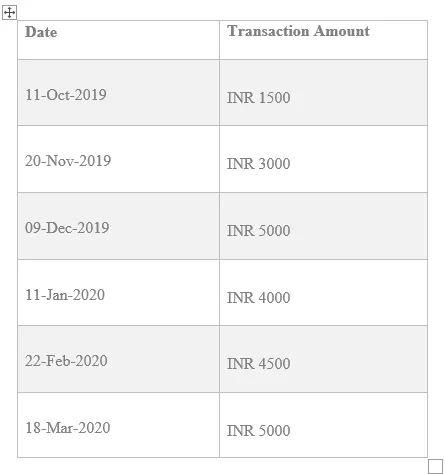
If the previous transaction ranges between INR 1000 — INR 5000 for the last 5 months and, if the user has prompted a value not ranging between the history, say INR 1 lakh, an unusual pattern is detected.
2. Geographic location is obtained using the IP address
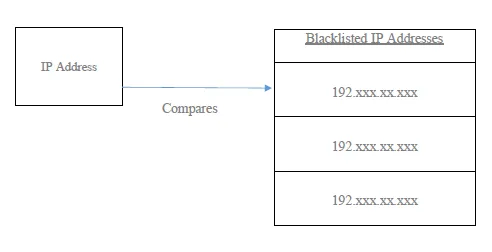
The IP obtained can be cross-checked with the blacklisted IP list. The location obtained is checked with the credit card owner’s previous location history. If any mismatch, an unusual pattern is detected.
3. AVS is performed
AVS is cross-checking the billing address provided and the credit card linked address for a mismatch.
4. Computer Details are verified
With the help of IP, machine detail is also fetched to check with the credit card owner’s machine history for any conflict.
5. Negative Database Security is performed
The details entered are checked with the negative database for any match, and if found, declines the transaction.
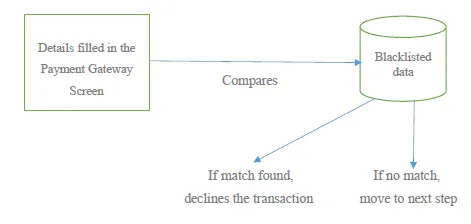
If any unusual pattern is detected, the system prompts you to re-login with credentials and a security question to be answered. The system even blocks the user for more than 3 invalid attempts and blacklists the IP and blocks the account.
In short, the secured payment gateway application uses User Behavior, Location Scanning, AVS, Device Identification and Negative Database Security to check for unusual patterns. Also, all data used for this application is well encrypted using AES and stored in the database and decrypted for further use to prevent SQL injection or any other attacks.
Scope Of the Solution
The scope of the solution is to develop a secured payment gateway and demonstrate how to prevent/minimize online fraud transactions using genuine card details and give an insight to the world on the importance of secured payment portals.
Another objective of this attempt is to enlighten all technology wizards to cook up new ways to face this issue reduce online fraud and make it safer for payment transactions via gateways. Also, all e-commerce websites should start thinking about integrating with a secured payment gateway to gain customer trust i.e., apart from financial losses, online fraud has a substantial impact on the image of the company too. Implementing such a secured payment gateway will not only reduce/minimize the potential losses but will also help to protect the company’s reputation as well.
Future Scope and Further Enhancement of the Project
- This project can be further developed to support other Operating Systems and can also be made mobile-compatible.
- During re-verification, instead of security questions, biometric authentication can be brought up for better security.
- In addition to Behavior and Location Analysis, Address Verification Service, Device Identification, and Negative Database Security, there are many other popular indicators available for fraud detection and those can be incorporated into the application for better detection and security.
- This application works based on previous transaction history and if history is not available, then the first transaction is considered to be genuine. So, such a loophole needs to be addressed in the future for better security.
- There are chances for cyber attacks such as IP spoofing that need to be addressed.
Thank you for reading! I hope you enjoyed it.

Hope you got a theoretical insight.
This is not a real payment gateway. It’s a project to address existing security flaws and some additional features that could be incorporated in the back end to tighten up their security and reduce fraudulent transactions at least by 30%.
Part 2 is its working demonstration. Click on the link below 😊
BLASEC : A PAYMENT GATEWAY – Part 2/2
If you liked it, do give it a shout, and if you wish to take up an initiative and reduce such online frauds and make it safer for payment gateways, do share it with your friends or colleagues.
Well, there are a lot of areas for improvement in this project and, for any new suggestions or comments, I’m all ears.
Download project from: https://github.com/sharuroy16/blasec
